As per reports by Statista in the year 2022, around 422 million individuals have experienced the instances of cyber-attacks in the USA, which is a matter worth concerning about. Some of the biggest reasons behind it are data exposure, data leaks and data breaches.
These security threats tend to impact various websites from small or big. Here, we will discuss some of the best MERN stack security checklists that you should essentially know about:
MERN Stack: What is it?

[Image Source:https://bit.ly/44wXp52]
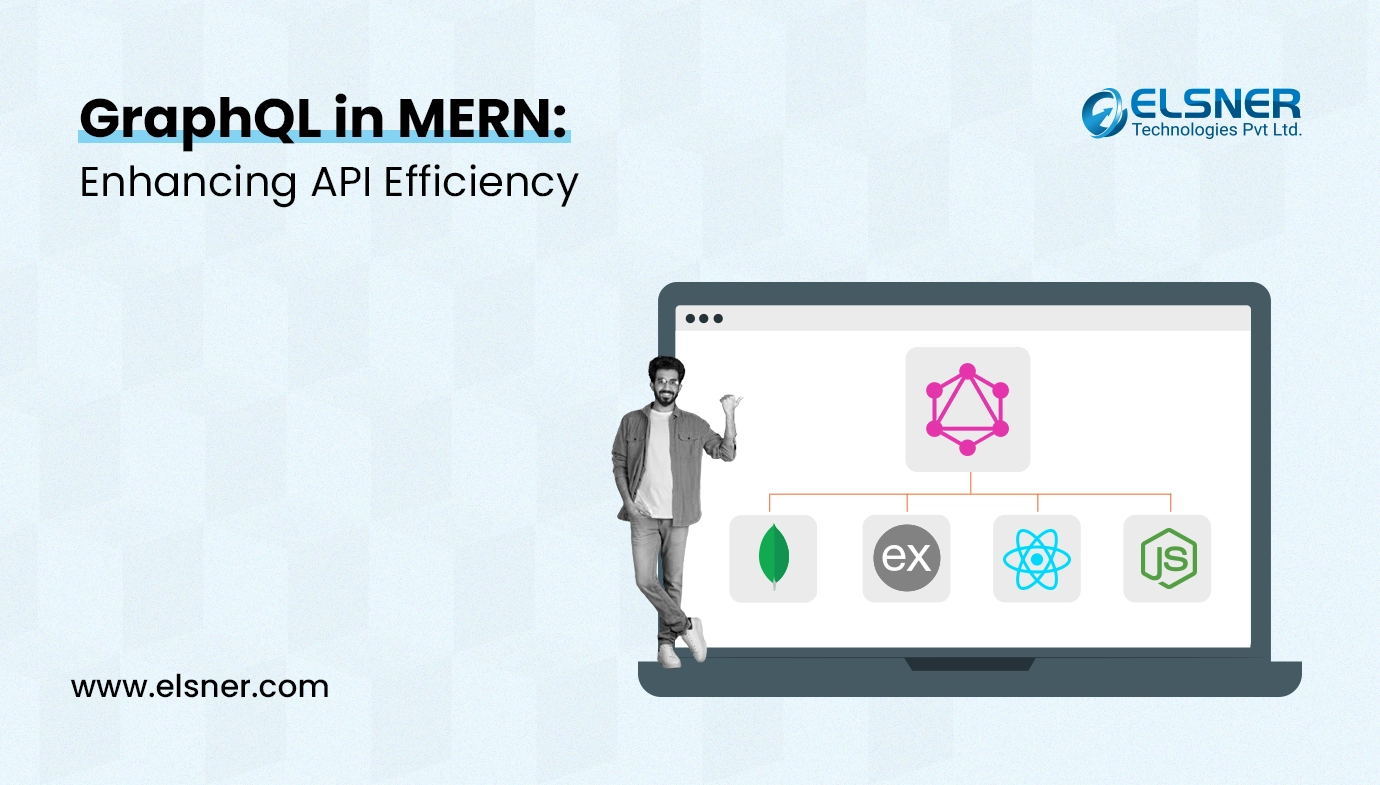
The combination of four popular technologies including MongoDB, Express.js, ReactJS and Node.js is known as MERN stack. It is indeed a powerful collection of technologies that facilitates swifter app development.
The primary purpose of leveraging it is to develop MERN stack applications by utilising JavaScript only. MERN Stack is again most commonly employed to create data-driven, complex and dynamic web apps.
As it is primarily designed to make the overall development process more manageable and smoother, it is used by developers across the globe.
Each of the robust technologies used to create the MERN stack offers an end-to-end framework for the developers to work in. All of these technologies also play a pivotal role in the development of web apps.
Now, let’s move further in our discussion by having a close look at each of the four components of MERN, along with its best security practices:
What are the 4 Important Components of MERN?
1. MongoDB
MongoDB is regarded as a NoSQL database that is efficiently designed to handle considerable volumes of unstructured data. It is typically employed to create highly scalable and available internet applications. Also, this document-oriented database facilitates storage of data in a JSON-like format.
Security Checklist
You should look for ways to effectively prevent unauthorised entry. One of them is to restrict remote access to the database. This way, you would be able to prevent the risk of data breaches. For further bolstering the security, you can choose to whitelist certain IP addresses to establish remote connection.
This database provides a wide range of authentication methods from LDAP to x.509 to SCRAM. It is important for you to make use of a solid mechanism. Also, you should focus on creating distinct users with varying roles which helps in effectively limiting access.
It is important to stay current by considering updating your MongoDB software on a frequent basis. It is a great way to stay away from any sorts of vulnerabilities and ensure that your database remains secure.
Another important thing is to keep a close track on any unusual activity like high disk usage, unknown IP addresses, etc.
You can even consider upgrading to the MongoDB enterprise model, which possesses several features that are not possible to access on the community version.
2. Express
If you are looking forward to creating RESTful APIs with Node, then it is suggested to rely on Express which is a recognized backend web app framework. It allows developers to come up with customized APIs along with middleware that best suits their project requirements.
Also, it eases the overall process of web application development by providing you with a diverse range of functionalities and tools.
So, this framework is typically employed for the development of distinct types of MERN stack applications, from multi-page to single-page to hybrid.
Security Checklist
The first and most important thing you should do is transition away from the outdated versions of Express, which are no longer helpful. It includes versions 2 and 3. So, if you want to see a considerable performance improvement, it is essential to migrate to Express 4.
Your utmost priority should be to use HTTPS instead of HTTP for establishing secure communication between the server and client. To further improve your application’s security, you can even consider employing Helmet.js.
Another fantastic way to ensure the safety of your app is by sanitising user inputs. For this purpose, you will require a validation library such as Joi or express-validator for mitigating the risk of Cross-Site Scripting (XSS), SQL injections and other potential vulnerabilities.
There is another valuable method for verifying user inputs, which is the express-validator. It comprises a collection of Express.js middlewares incorporating a sanitiser and validator.js function, improving input verification and overall security.
3. ReactJS
Originally developed by Meta, ReactJS is a front-end JavaScript library that has gained much recognition. It is mainly used for the development of user interference that is based on components.
ReactJS is designed efficiently to construct reusable UI elements, making developing intricate user interfaces or UIs more straightforward. It is primarily used to facilitate the building of interactive web apps and UI quickly. The best part is that, in this case, the coding requirements are much less.
A MERN stack developer can rely on the available React development tools for achieving a swifter web application development procedure.
Security Checklist
If you want to mitigate the risk of DDoS (Distributed Denial of Service attacks) it becomes essential for you to put restrictions on the number of requests from a specific IP address. Also, you should ensure that the calls originate from the server instead of the client.
Another important thing is to use JWT tokens to facilitate the effective management of sessions. By ensuring this, you could prevent cross-site request forgery attacks. Also, ensure that your application exclusively reads CSRF tokens to improve security.
One of the best approaches you can adopt for securing your platform from crashing is to use 2-step and multi-factor authorisation. These specific measures help prevent unauthorised access and the exploitation of credential data. In turn, it effectively lowers the risk of system crashes.
You can reduce the chances of potential vulnerabilities by regularly updating 3rd party dependencies and packages. Also, you should essentially make sure to keep your code base current.
You should follow the best MERN stack security measures to ensure maximum protection. As a part of it, you should ensure that your sensitive data is encrypted well when stored and transmitted over the network. It helps in strengthening the overall security.
4. Node.js
Node.js is a cross-platform and open-source run-time environment that seamlessly operates on a wide diversity of platforms. It includes macOS, Unix, Linux, Windows and a lot more. Essentially, it works as a backend language known for executing codes outside the web server.
It is again recognised for its non-blocking I/O model, which signifies that it can handle multiple requests all at the same time without blocking the event loop. Additionally, Node.js boasts outstanding scalability capabilities, making it a highly sought-after option for developing large-scale web apps.
Security Checklist
If you want to stay protected from brute-force attacks, it is highly suggested to strengthen your authentication system. You can also implement mechanisms for preventing the number of login attempts from a sole IP address. It will help in the detection of any potential vulnerabilities that are resultant from such malicious activities.
You should make sure to carry out the implementation of input validation and sanitise user input. It is an effective security measure as it will aid in preventing Cross-Site Scripting (XSS), SQL injection and other common attacks.
One should never overlook the importance of closely monitoring the data transmitted to the front end. In this case, you can use many encryption techniques to secure sensitive data.
You should refrain from using Node.js in-build crypto library if you want to create a solid authentication policy. Instead, it is suggested to use Bcrypt or Scrypt libraries in this case.
Another vital thing involves setting up a cookie flag such as HTTP only, or else you can focus on improving session management security.
However, it is vital for you to keep in mind that security is a continuous procedure. So, one should always keep up with the latest version. Finally, you should follow all the MERN stack security best practices mentioned in the above section to accomplish the desired outcomes.
In a Nutshell
MERN is undoubtedly the ideal choice for developers looking forward to creating high-end web applications. However, you must follow the above-discussed security best practices to protect your platform from data breaches.
Along with that, you should also frequently assess and improve the MERN stack security measures in place to offer protection to your web app against potential vulnerabilities.
When needing a scalable and fast web app for your business, you should approach a professional MERN full stack developer with related expertise in producing goal-oriented outcomes.

About Author
Tarun Bansal - Technical Head
Tarun is a technology enthusiast with a flair for solving complex challenges. His technical expertise and deep knowledge of emerging trends have made him a go-to person for strategic tech initiatives. Passionate about innovation, Tarun continuously explores new ways to drive efficiency and performance in every project he undertakes.