Wondering what this hilarious word mean? This is actually an attack that can be very destructive for your WordPress website. But What is it? Wait! I ‘ll tell you!
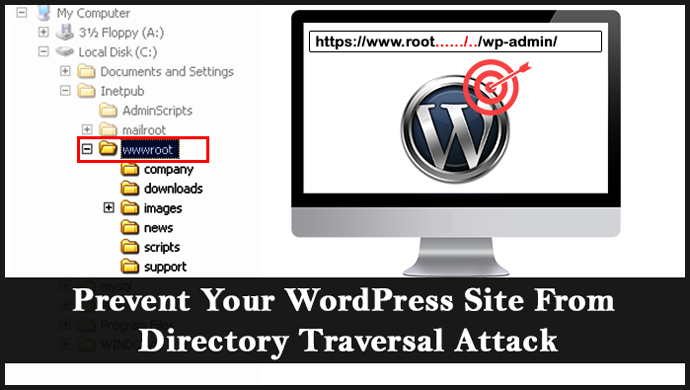
Also known as path traversal attack, a directory traversal attack is a brutal attack that can be done to the root directory of your website. Management of the control access to a web content is a very crucial thing for running a secure web server. A directory traversal attack is basically an HTTP exploit that can allow the attacker to access the directories of your WordPress website and execute commands that are not suitable for your server’s root directory. In exploiting insufficient security validation of the input file names so that characters that are representing “traverse to parent directory” are passed through to the file APIs.”.
When you are using secure web servers, they will provide two levels of security mechanism.
Access Control Lists
An Access Control List is used at the time of authorization process, it is used by the server admin to indicate the group of people to provide access and let them modify certain files on the server along with other access rights. It determines which user is privileged to access the files on the web server.
Root Directory
This is a directory on the server in which users are confined and are not allowed to access anything out of this root directory.
Wondering when it can occur to your website?
When the user-supplied input is not filtered properly, the attacker gets a chance to attack the directory of your website. There is some data that is compulsory to filter before processing it. Here we go!
- URL Parameters
- FORM Parameters (GET and POST parameters)
- Cookies
- HTTP Request Headers
How The Attacker Does It?
The attacker might have various ways to attack the directory of your website. But the maximum used way is they enter special character “../” sequence which will let them escape the web document root. They can also use the encodings of “../” sequence in order to bypass security filters and access files residing outside the root directory.
Once It is done, What Attacker will be able to do to your website?
The attacker will be able to reach out to the restricted files and directories of your website. The critical files such as libraries, programs or downloaded files can be modified and edited by the attacker once he becomes successful in attacking your website. He will now be able to expose the source code of your web application or execute powerful commands on the web server.
The path traversal vulnerability exists in the file ajax-actions.php, in particular in the function wp_ajax_update_plugin().
Looking for the ways to avoid this attacker from ruining your website?
Here, you will find some points that you should keep in mind in order to avoid this attack on your WordPress website:
WordPress Authentication Unique Keys and Salts Are Important
Keys and Salts are the things that can easily lead the attacker to your root directory. Once any of them gets to know them, they will easily be able to get into your dashboard.
SQL Injection is Also Crucial
If your Tables prefix is revealed, they can help the attackers to attempt the attack.
MySQL Database Charset Should Not be Revealed Either
There are some attacks that majorly depends on this information. Don’t Share this Ever!
Login Credentials Are Always Important
Either it is your social media account, or your bank account or your website, login credentials are something that must not be shared by you ever. Never make the foolish mistake of keeping the username and password same. Attackers are the ones who are aimed at destroying your website, they will try to login on the FTPs, on your emails, social media with a lot of variations in the passwords, so if you have even kept some easy one, they will get into it. Though they won’t be able to access the database, they can try to enter into the directory by anyways if they even have some hint. So never share the login credentials with anybody and also, keep them complicated.
You can also make sure the safety of your website with the help of some good security plugins and methods available out there in the huge world of WordPress Plugins.
Facing any such issue on your website?
Here we are, to help you out with this!
As a leading WordPress development company, you can contact us to secure your websites from such issues.

About Author
Pankaj Sakariya - Delivery Manager
Pankaj is a results-driven professional with a track record of successfully managing high-impact projects. His ability to balance client expectations with operational excellence makes him an invaluable asset. Pankaj is committed to ensuring smooth delivery and exceeding client expectations, with a strong focus on quality and team collaboration.