Majority of people across the globe today have smartphone devices in their pocket. Due to this increased popularity, it has become an easy target for hackers. As a result, app security has become a very prevalent issue. Today, security of mobile apps has become a pertinent issue globally. You can see it on the news where there have been instances of hackers exploiting loose ends in the mobile software to misuse critical information, spy on the users or even steal money.
In order to stop this activity, security companies have not resorted to an advanced technique known as “application shielding”. It is nothing but a process to complicate the mobile application’s binary code to supposedly make it harder for hackers to reverse-engineer.
In the forthcoming sections of this write-up, we have tried to throw light on the various aspects of app shielding in the practical world that can work for the betterment for mobile app development companies while they are providing the mobile app development services. We promise after reading this content piece you will have relevant information pertaining to app shielding during the mobile app development process.

Before we move to the business end of this write-up it is extremely important to understand where exactly can application shielding can be helpful in the practical life. With the aid of “application shielding” it is possible to protect the intellectual property and ensure that there is no piracy, which has become a great headache nowadays.
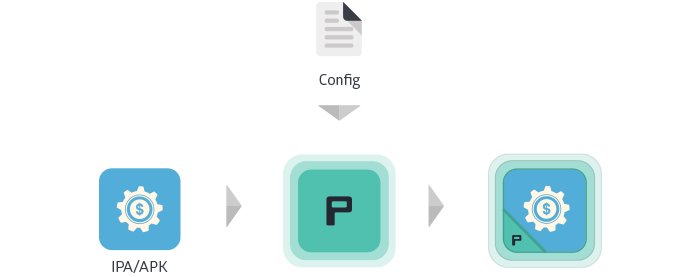
The process commences with the modification of a service’s application code which makes it extremely difficult for someone to tamper with it. With the help of “app shielding” it becomes extremely hard for hackers to get access to the digital rights locks and steal medias easily.
Now that you have understood the concept of application shielding, let us divert our attention to the practical application of app shielding during mobile development.
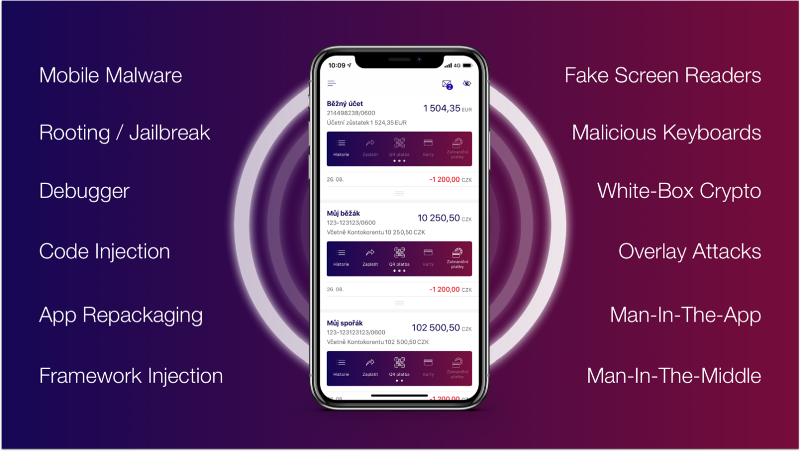
As time has passed, the term “app shielding” has evolved. It now includes various other features too. It is also known as “binary protection”. With the help of this shielding, it is possible to run validity and integrity checks which ensures that the mobile app is running in a safe environment which cannot be tainted. In practical world, you can see it in the form of biometric authentication checks. These checks make it difficult for hackers to analyze a mobile app’s binary in order to find ways to attack it.
While these mechanisms can act as a boon to strengthen the mobile app defenses, the concept of “app shielding” is still evolving as we write. Some of the obvious benefits that claim to stop hackers by stopping a mobile app’s binary code might be overstated. With time, you will see these techniques advancing which would bring out an altogether new security threats emerging for the users.
This way, you will see more and more financial enterprises and other high-value environments employing it to secure their mobile apps. But, other tactics like confusing the hackers will not be extremely helpful. Reason? An attacker will be able to get to learn everything about the system without having an opportunity to exploit it to their advantage. A shielding code is more like hiding a treasure behind a painting. If you have a secure look, it doesn’t matter who is able to see it.
If you look at banks, stock brokerage firms, and retail banking, the one thing that you will find that they are not mystifying their code. In case, you are introducing a mobile app out on the Google store. There is every opportunity for hackers to exploit it to their advantage. Due to lack of research by mobile security professionals, there is every chance of carelessness which results in security missteps which mobile developers need to avoid at all costs. But, there is every chance that the hackers are motivated enough to get past the obstruction that you have laid on their path in terms of codes. So, if you have a skillful hacker there is every possibility for them to achieve their objective.

You can even use shielding in the context of cybersecurity. For example, today you have the option of storing your critical information, including data and applications in third-party cloud environments.
This way you can get the necessary flexibility and protect unauthorized access from getting inside your cloud storage. With the help of “app shielding” it will become easier to protect your data from untrusted cloud environments. Although, it is still at an infant stage you can expect further development in this regard in the near future.

You can even use application shielding as a layer of digital rights management so that you are able to satisfy the regulatory requirements or licensing formalities. It is highly recommended for companies that are working on video streaming services. There are times when not obfuscate the code is not a big deal in case of financial apps. Reason? It does not add any dimension to the security and be accessed without much trouble.
One problem with binary obfuscation is that it simply is used to enable mobile app developers to mask components of what their mobile app does. Many times hackers use malware to sneak past mobile app store screening by Apple and Google. By muddling with the code, a mobile developer might thing that they have safely protected their sensitive information which is embedded in the app. But, this is not true. For example, by putting a painting in front does not mean that you can leave it unlocked.

While performing app shielding during the mobile app development, use the best practices to authenticate the user. Scrutinize the integrity of the operating system, use cryptographic checks like confirm device identity or transaction signing which can result in enhancing the defenses of your mobile applications during the development phase. But, with time as the technology evolves, always remember that this is not a full-proof security app shielding plan that can be trusted for long. You cannot simply sit on the laurel and think that the technology will not upgrade. With time, the hackers will also become smarter.
The Final Countdown
Although, we feel that mobile applications are much easier to run on Android App Development or iOS App Development platforms due to simpler formation of codes, that is hardly the case. Most of the mobile apps function on par like websites. They run partially on phone and partially in the cloud. With the help of “app shielding”, it becomes difficult for hackers to hack the parts of the app that are run on your phone. The future course of action for mobile developers is to think about those parts of the applications that are on the cloud.

About Author
Tarun Bansal - Technical Head
Tarun is a technology enthusiast with a flair for solving complex challenges. His technical expertise and deep knowledge of emerging trends have made him a go-to person for strategic tech initiatives. Passionate about innovation, Tarun continuously explores new ways to drive efficiency and performance in every project he undertakes.